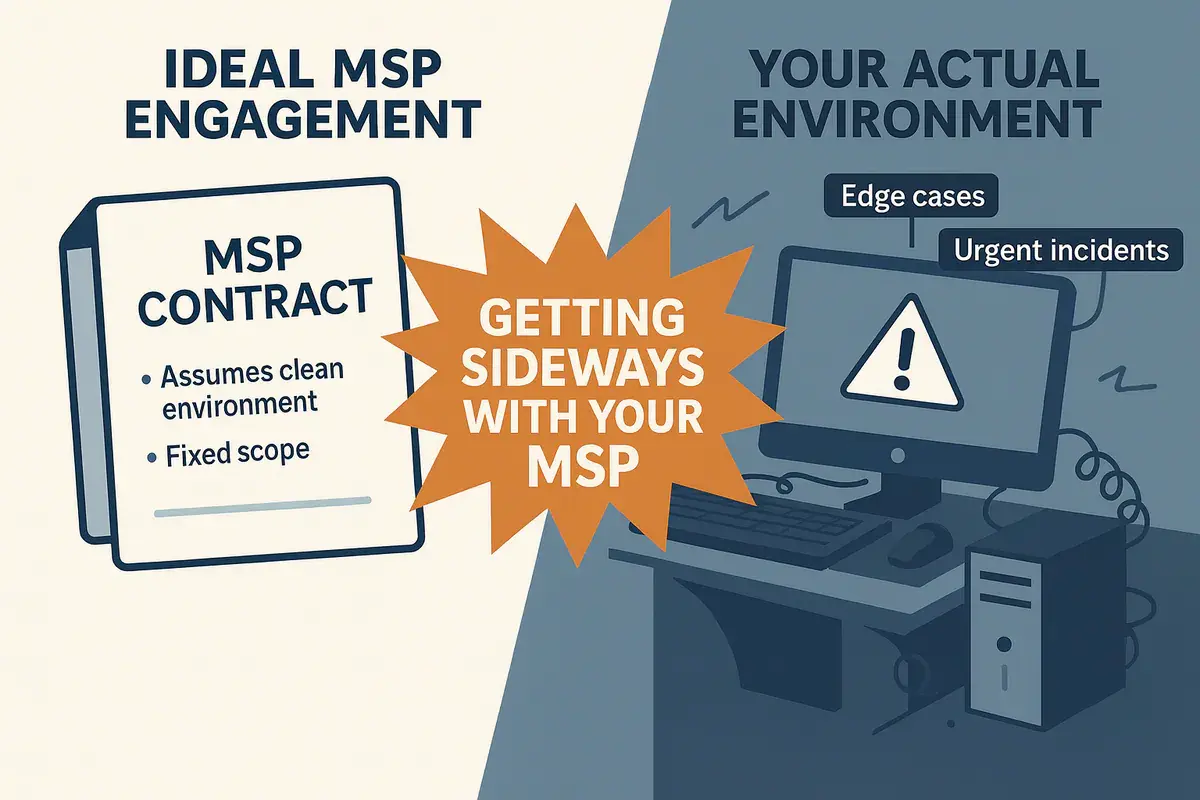
Why Do Fractional CISOs Get Sideways With Your MSP?
It’s almost a maxim around here: the more one of our clients needs an MSP (Managed Service Provider) for IT services, the worse the service fit and the security posture between the client and the MSP.
Think about that. Through the security and IT hygiene lens, it sounds like a fundamental MSP market failure. Isn’t the whole idea of MSPs to make the benefits of information technology available to businesses that can’t or don’t want to do it themselves? Over the five years that IOmergent has built and operated security programs for emerging midmarket companies and high growth startups, here’s what I have come to believe:
The MSP market as a whole does not inherently fix broken IT or provide good IT as a service, rather it marketizes the full spectrum of IT practices - from the completely buttoned-up environment to the raging dumpster fire.
And the relevant corollary to this theory is:
Many MSP customers go through the same IT and security maturation process that companies with internal IT and security go through - only some MSPs ease the pain.
Putting aside general dissatisfaction with MSP services that I hear from business and technology leaders, my admittedly anecdotal evidence for this corollary is the poor MSP service fit and generally lacking security posture we typically assess among our emerging midmarket clients that rely on MSPs. My sample is obviously biased. I know there are good MSPs out there but we rarely run into them in the field unless we are introducing them to one of our clients that is moving from a different and no longer tenable MSP relationship.
Bottom line: we routinely end up getting sideways with our clients’ MSPs. Our consultants ask uncomfortable questions and deliver related findings in security program assessments. Our Fractional CISOs, actively working with their clients to improve security posture, cause review of MSP contracts and service level agreements. In the worst cases, our assessments or Fractional CISOs flat out recommend that clients switch MSPs or insource the services.
Security In MSP Markets
I was chatting about security in the MSP markets a few weeks back with the head of product at the leading SMB cybersecurity firm and complaining about this phenomenon. We discussed how every edge case that comes up in security and hygiene can drain MSP margin (people and maybe bot-herders chasing down messy situations) when the MSP’s offering is not structured to handle them.
This product leader’s company enables MSPs to provide generally important aspects of IT security by supplying products like endpoint security packaged for use by the MSP channel. These solutions can improve MSP end customer security posture as long as they are properly installed and managed. Security solutions that sell through the MSP channel squarely address real security threats and thereby can reduce client risks, but not the risks associated with poor MSP service delivery and fit.
The White Glove Treatment
Let’s examine MSP service delivery and fit through the security lens a little bit more. The “good” MSPs from a security and IT hygiene point of view are - surprise - the white glove providers. These MSPs are foundationally looking out for their clients’ security and resilience. We’ve worked with MSP leaders who built and exited successful white glove MSPs. They introduce and sell extra security - their own services or third party services - when it’s necessary for their customers. We have also worked with larger service providers characterized by detailed and prescriptive operating procedures and service structures that require customer organization to transform in many ways when they implement.
These MSPs have to find educated subsegments of customers with the means and motivation to pay for and/or consume meticulous service delivery, for example:
- Tech companies with VC backing who want to ensure that IT services can support their ability to scale and that security and IT hygiene doesn’t interrupt sales or operations; or
- Segments of manufacturers or healthcare service providers whose organizations can endure highly structured managed IT environments with glacial change control processes but cannot accept a meaningful risk of loss from disruption due to ransomware.
And for the vast majority of small and medium sized businesses that won’t pay a premium for white gloves or transform sufficiently to leverage a highly structured environment?
The Wild West
One thing you can say about the MSP market is it’s wildly competitive. There’s a strata of MSPs that will give their clients exactly what they ask for and with attractive pricing. In some cases it simply means that MSPs are willing to provide scaled back services via what are otherwise very robust service delivery tools to companies that cannot or will not allocate the budget. In other cases, firms go to market like a flexible MSP but operate more like a business process outsourcer - inexpensive offshore labor executing the agreed IT work remotely.
Both of these MSP types can serve companies well when the companies understand what they are getting. But flexible and economical MSPs can run into problems when their customers realize that they simply did not have the expertise to ask or negotiate for better quality managed services during procurement. How do you tell a client after years of service that they did not pay for DR testing when it never came up before? Successful MSPs in this strata constantly manage expectations over the arch of their customer relationships.
Of course there are also truly bad MSPs. Some bad MSPs are small businesses with talented individuals and good intentions that simply can’t deliver on their promises and never achieve operational excellence.
Their more malevolent cousins are well-funded MSP marketing machines. They advertise strong security outcomes - among other things - and point to their SOC-2 attestations. Under the covers, they are structured (only certain service delivery routines really work) but externally they have fuzzy service boundaries (intentionally nebulous - perhaps to boost sales).
Bad MSPs feed upon organizations that care about security and resilience conceptually but don’t, or can’t, track performance or even read their MSP’s reports until there’s a serious problem. If bad IT hygiene is normal for you, these MSPs deliver. The annoying edge cases are ignored through lack of service maturity or, worse, by design and unknowing MSP customers are none the wiser. Customers that wise up - often with the help of a Fractional CISO, CTO or CIO - tend to churn.
Recommendations For MSP Market Participants
Consider these recommendations if you want to avoid getting sideways in an MSP relationship:
For MSP End Customers:
- Evaluate your security, resilience and cyber risk on a periodic basis
- Evaluate the internal security and resilience of MSPs during procurement
- Evaluate whether an MSP’s service will improve your resilience and reduce your cyber risks
- Actively manage your MSPs throughout the service relationship
- Pay attention to MSP service boundaries, tickets and reporting
- Leverage external resources like fractional CISOs, CTO or CIOs if you don’t the experience in house
Remember, you get what you pay for!
For MSPs
- Stay current on best practices for security and resilience
- If the long term relationship matters, tell your customers when you must provide less than best practice security in order to hit their price expectations
- Delay the SOC-2 and invest in improving your security and resilience practices first
- Upsell security solutions - plenty of vendors that want to help you secure your customers
- Leverage external resources like fractional CISOs internally and externally
Remember, it’s an insane market and churn can kill MSP businesses!